Is Your Business Tied Down By

Data Sharing
Limitations
Most businesses refrain from sharing their data that could lead to better data driven decision making as sharing data increases the risk of exposure and breaches. Some even avoid cloud migrations due to security and compliance concerns—often leading to underutilized, misconfigured and siloed data.

Poor Database
Encryption Posture
While most databases offer integrated encryption capabilities, the security and compliance of the database relies on secure storage, policy management and audit logging of database encryption key access and it’s availability across multiple sites globally.

Need for Application-
Level Encryption
Encryption is the only way developers can keep their apps secure. Developers also need to add in additional layers of security. They need to think about how the app data is being accessed and provide strong authentication controls.
The Fortanix Difference
Fortanix Solution
Fortanix Data Security Manager (DSM) provides built-in Hardware Security Modules (HSMs), to securely generate, store, and use cryptographic keys or other secrets, such as credentials and certificates.
As a centralized solution, all administration and cryptographic operations are securely logged can be exported to external SIEM solutions. The Fortanix platform has NIST 140-2 Level 3 validated security, and keys are generated from a high-quality source of random data as recommended by NIST SP800-90A.
Fortanix DSM can be deployed either as an on-premises solution or leveraged as a SaaS offering.
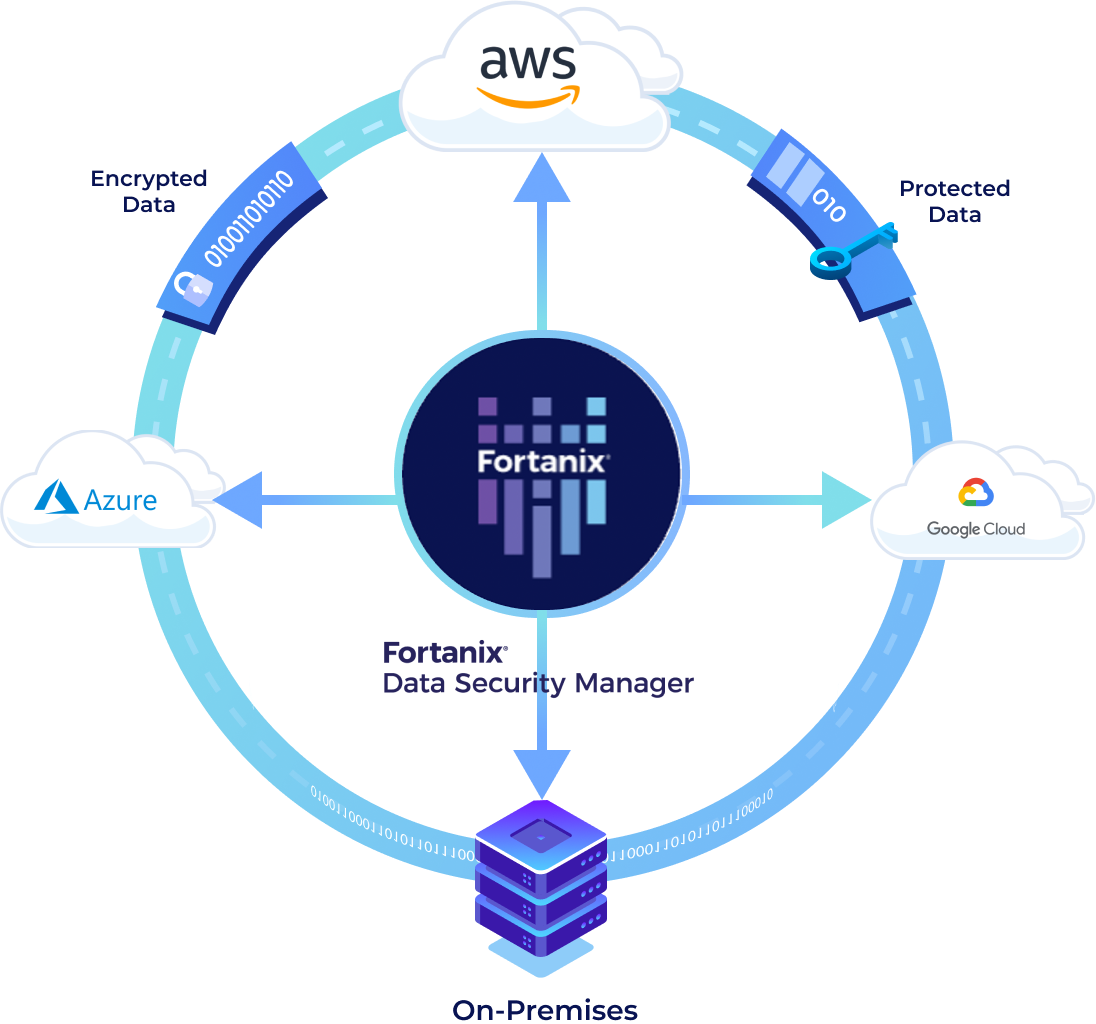
A Pervasive Data Security Solution
Deploy a pervasive encryption strategy across hybrid and multi-cloud environments. A centralized set of data security solutions enable full control of all your encryption keys to manage their lifecycle and cryptography posture.
Break The
Data Siloes
The centralized Fortanix DSM platform manages your encryption keys and enforces uniform access control policies for your data, regardless if your data resides on-premises, or in one of the leading Cloud Service Provider platforms.
Simplify All Cryptographic Operations
The unified DSM platform simplifies all your cryptographic operations. With an intuitive graphical user interface, or a RESTful API for power users, your developers and security teams can control and audit data security across any environment. The platform is easy to deploy as a SaaS and provides a rich set of integration options.
Flexible Deployment Options
On-Premises or In the Cloud

